What do you usually do when you lost the password of the security cameras and recorders?
- Hikvision’s password reset policy encountering a security vulnerability
When you start security products at first, you usually set the new password which meets the complexity requirement to enhance the security.
Password complexity is essential for security reinforcement, but if you lost your password, it is too hard to figure it out and sometimes there is no other option than a factory reset (it applies to Hanwha Techwin’s products).
Recently I found out the easy way to reset the password of Hikvision products.
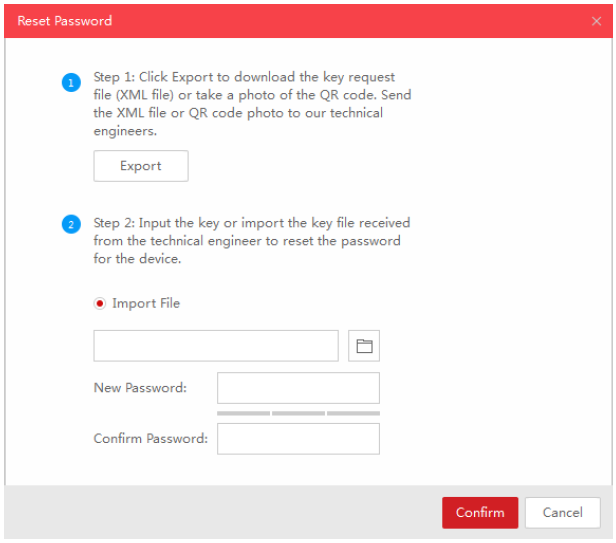
After losing the password, I was about to do a factory reset, but I couldn’t find the reset button. I contacted the Hikvision support center and got a tool called SADP Tool for password reset.
It is easy to use.
You first install the tool on your PC, search the relevant device, and export the ‘Key request file’, Then fill out the both user and product information and send email to the support center. When you receive ‘Key file’, import the file using SADP Tool, and then password reset is done.
The user info you should give is your name, email address, phone number, and company name. You also should provide device info such as the firmware version, serial number and other date and time info, which you can get easily when you check SADP Tool.
There is no doubt that SADP Tool is easier than a factory reset. However, it is fact that any other people who get access to SADP Tool can easily reset the password and control my system.
Furthermore, what happens if anyone sends the false user info out of spite?
With curiosity, I created a fake user and sent spoof user info such as name, phone number, company name, address, etc. with my device information to the Hikvision support center. Do you know what happened? They sent me ‘Key file’ before the day passed!
The manual says that you should not reset the device after exporting the ‘Key request file’ and the ‘Key file’ you received is valid only within 24 hours. But these restrictions do not mean much, I think, and anyone can easily get the ‘Key file’ to reset the password of Hikvision products.
If I take this issue a bit seriously, the manufacturer (Hikvision) may be able to remotely reset the password of their products whenever they want only with limited info such as the firmware version and serial number. And if that is true, you may have a very serious security vulnerability hidden in the back of user convenience.
I am not writing this to attack a certain company. I wish we all – security product users, manufacturers, installers and more – have chance to be concerned about the password reset policy to reduce security vulnerability.
Feel free to give your opinions. Thanks.